Describe Tools Used to Attack Web Servers
DDoS attacks use an army of zombie devices called a botnet. Server-side attacks work against a normal computer websites web servers people as long as we can ping them.

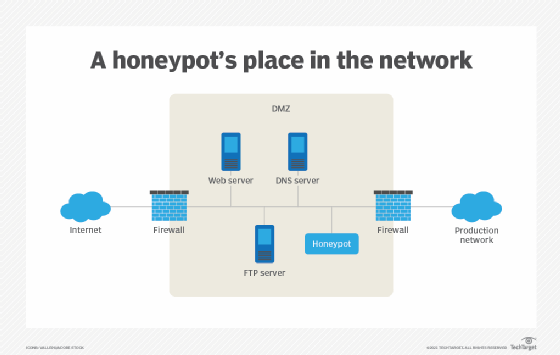
Perimeter Network An Overview Sciencedirect Topics
John The Ripper is the popular password-cracking pen-testing tool that is mainly used to execute dictionary attacks.
. Use only approved public algorithms such as AES RSA public key cryptography and SHA-256 etc. Since 2018 security breaches have increased by 11. The FTP bounce attack is used to slip past application-based firewalls.
Designed to send small amounts of data across multiple connections in order to keep ports on a targeted server open as long as possible these tools continue to take up the servers resources until it is unable to. Customization of apache web server is easy as it. With an SQL injection attack criminals can gain access to your database spoof a users identity and.
Apache is an open source software which supports almost all operating systems including Linux Unix Windows FreeBSD Mac OS X and more. As the name implies these types of attack tools use a low volume of data and operate very slowly. About 60 of machines run on Apache Web Server.
These vulnerabilities may later be exploited using tools or manually. Explain that frameworks are typically called on for a specific purpose and are designed to make. Just to convey this idea we will see the Metasploitable machine.
Web applications check URL access rights before rendering protected links and buttons. Collections of compromised systems commonly used in DDoS attacks. Using the -ls command we can list it and we can even install a graphical interface.
Many of the servers that store sensitive data use SQL to manage the data in their database. The DDoS attack will test the limits of a web server network and application resources by sending spikes of fake traffic. Internet Information Service IIS and Apache are commonly used web servers.
This tool can also be used to carry out different modifications to dictionary attacks. Provide at least three methods or tools used to attack web servers as well as provide how each of these three methods can be. Every attacker tries to gather as much information as possible about the target web server.
Lets look at how your organization can protect itself against web server vulnerabilities attacks. One of the most popular web server in the world developed by the Apache Software Foundation. Some attacks are just short bursts of malicious requests on vulnerable endpoints such as search functions.
As hackers find more sophisticated ways of accessing your data security is becoming a day-to-day struggle for businesses. Apache web server. Describe Web applications 2.
It has been awarded for having a good name. Separate Development Testing Production environment. Making the audit easier.
These include Memcached used to speed up database and web-based transactions the DNS server the NTP and the SNMP. Monitor and audit the server. The purpose of this attack is usually to flood internal buffers and queues in the web server and even in the mitigation devices in front of it.
And in the first half of 2019 alone 41 billion personal records were exposed. It is just a normal virtual machine that we can use right here to do anything we want. Failure to restrict URL Access.
The penetration tester is able to gain rootadministrative access in several servers by exploiting vulnerabilities associated with the implementation of SMTP POP DNS FTP Telnet and IMAPWhich of the following recommendations should the penetration tester provide to the. An SQL injection uses malicious SQL to get the server to expose information it otherwise wouldnt. FTP File Transfer Protocol is used to transfer documents and data anonymously from local machine to the server and vice versa.
It is often referred to as John. And losses due to data exfiltration stolen IP and ransomware are also accelerating at a fast pace. Web server logins should be stored in a separate area.
All applications can easily be found by unwanted users. Attackers advantage of the networks web servers and misconfiguration and bugs in the operating system to attack against web servers. This is a huge cyber risk if the database stores customer information credit card numbers credentials or other personally identifiable information PII.
All administrators of FTP servers should understand how this attack works. Ensure offsite backups are encrypted but the keys are managed and backed up separately. Discuss securing web applications.
These are some common tools used in DDoS attacks. The attacker gathers the information then analyzes the information so as to seek out lapses within the current security mechanism of the online server. Common Web Server Vulnerabilities SQL Injection.
The attack is also sometimes used to saturate the internet pipes although there are easier attack techniques to do that. This way website access network services database server and operating system logs can be monitored frequently. Describe the use of Web forms to allow users to send information that can be processed by Web applications at the Web server.
Review the tools used to attack Web servers. SQL injections are one of the first security vulnerabilities attacks cybercriminals try to gain access to your system. Describe the tools used to attack Web servers 4.
Network devices include items such as routers and switches. Acunetix Nikto Vega etc. 500 words or more please.
GET flood the most common usage of the HTTP protocol is an GET request. The results may show various threats and vulnerabilities on the target web server. Apart from the generic firewall there is an advanced level of security that needs to be implemented to ensure complete safety of the web servers.
A web server can be hacking using these hacking tools like ZeuS Neosploit and MPack. Low and slow attack tools. This attack is also called URL poisoning as the attackers manipulates the URL by changing its semantics but keeping the syntax intact.
Identify web application vulnerabilities and tools used to protect web servers. The GET flood uses the same. The parameters of the URL are adjusted so that.
An organization has hired a penetration tester to test the security of its ten web servers. There are automated tools for scanning a web server and applications running on it.
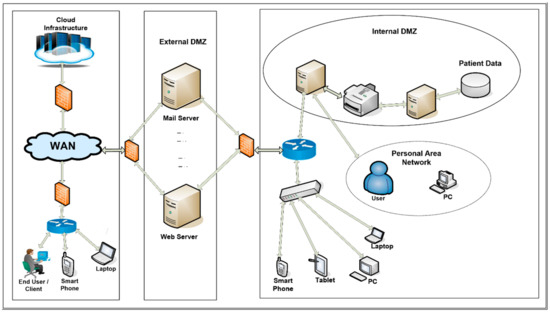
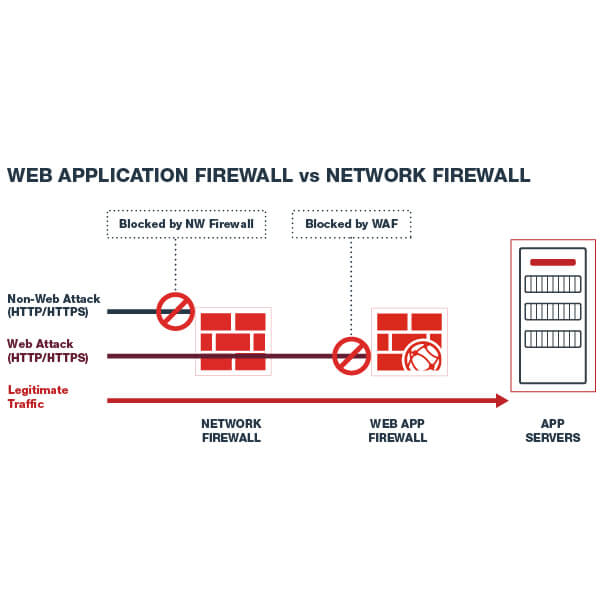
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html
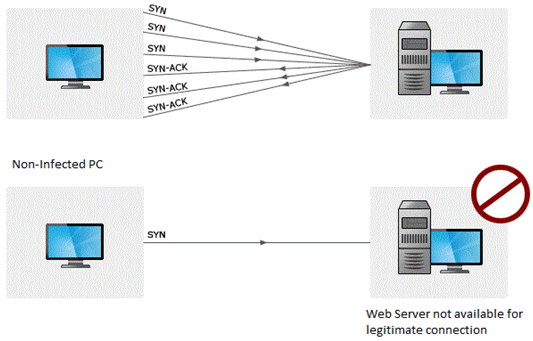
Web Server And Its Types Of Attacks Ethical Hacking
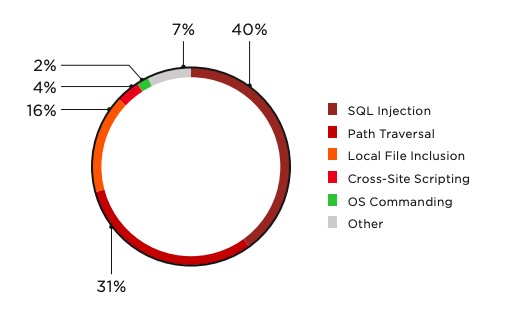
Web Application Attacks 2018 In Review Web Based Attack Types And Trends
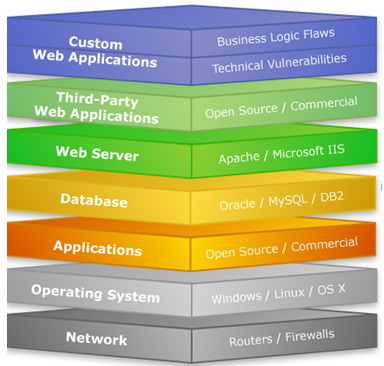
Web Server And Its Types Of Attacks Ethical Hacking
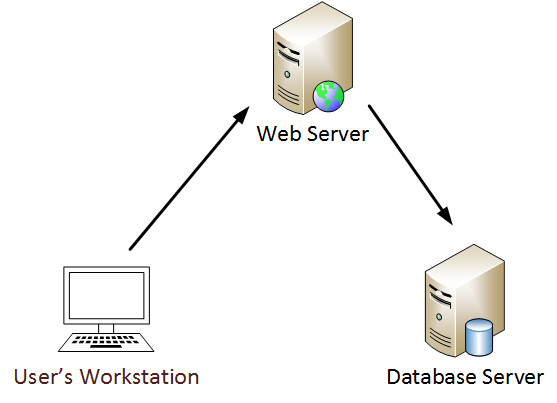
Active Directory Security Risk 101 Kerberos Unconstrained Delegation Or How Compromise Of A Single Server Can Compromise The Domain Active Directory Security

Web Server Attacks Infosavvy Security And It Management Training

Free Interactive Secure Development Training Snyk Learn

Web Server Concept Infosavvy Security And It Management Training
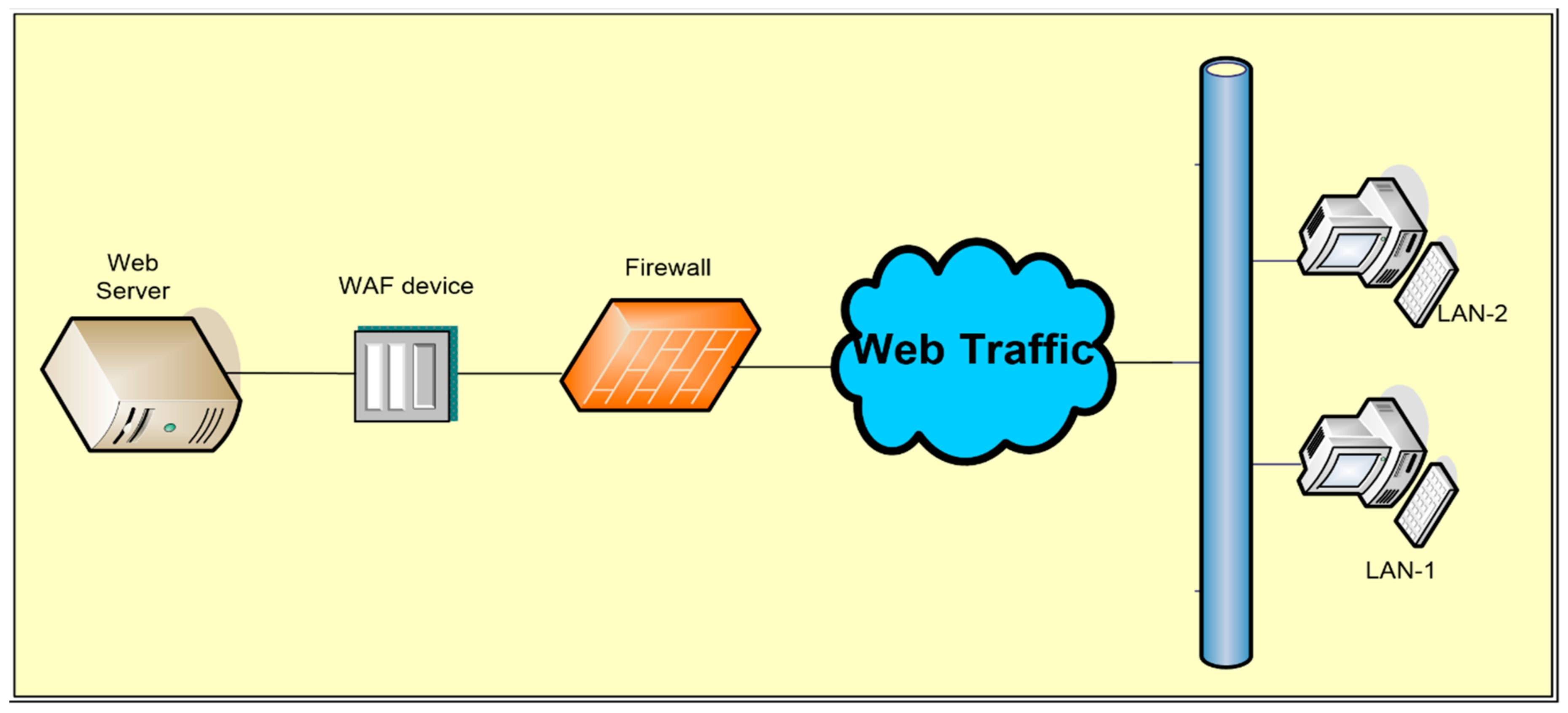
Applied Sciences Free Full Text Firewall Best Practices For Securing Smart Healthcare Environment A Review Html

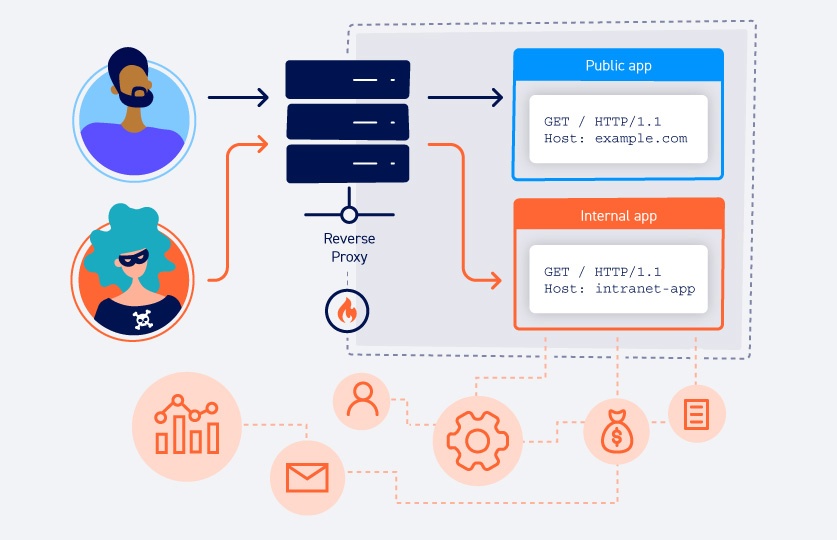
Http Host Header Attacks Web Security Academy
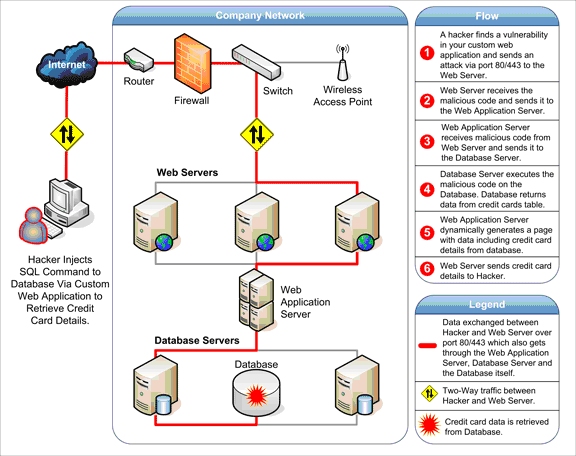
Web Application Attack What Is It And How To Defend Against It
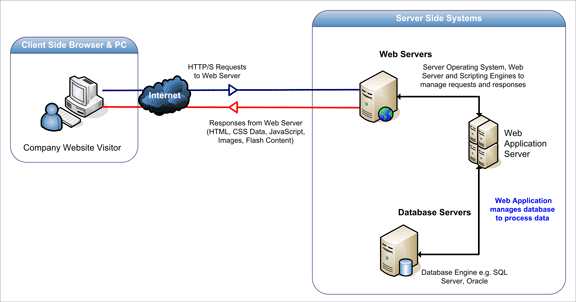
Web Application Attack What Is It And How To Defend Against It
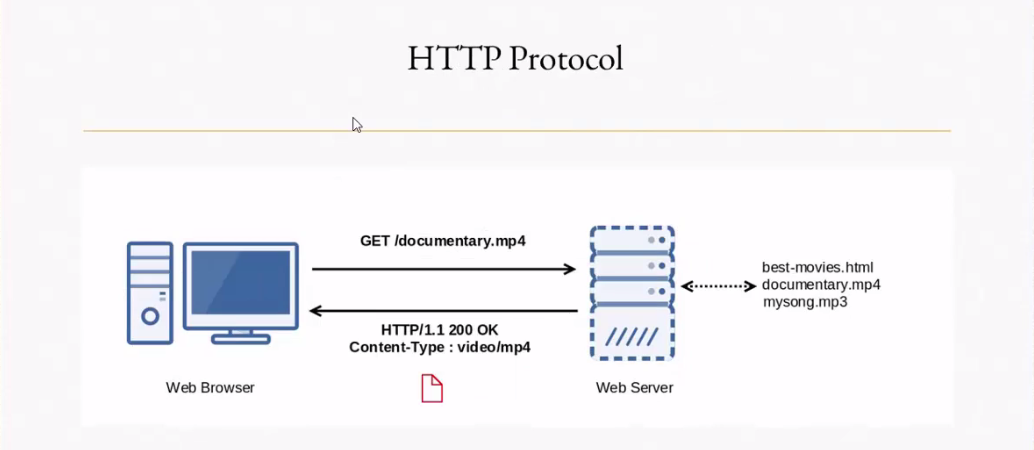
Nginx Webserver With Basic Http Protocol By Sanjeev Gautam Medium
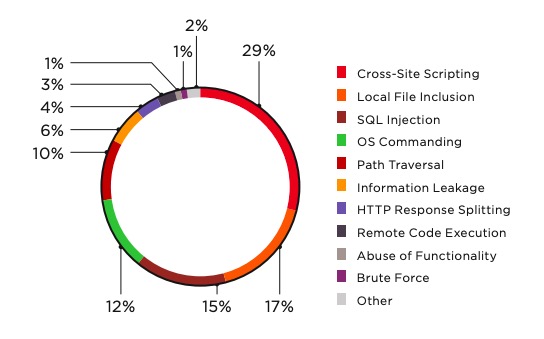
Web Application Attacks 2018 In Review Web Based Attack Types And Trends

Multitier Architecture An Overview Sciencedirect Topics

Server Side Attack An Overview Sciencedirect Topics
Comments
Post a Comment